THM | Red Team Engagements

Red Teaming | Red Team Engagements | Summary:
This room serves as a guide for Red Team engagements, covering essential steps such as defining scope and objectives, establishing rules of engagement, and planning campaigns, to ensure successful execution and effective documentation of the exercise.
It provides a structured approach to setting up and conducting a Red Team engagement, from conceptualizing the project to executing it, including key operational plans and mission-specific details.
Disclaimer: Please note that this write-up is NOT intended to replace the original room or its content, but rather serve as supplementary material for those who are stuck and need additional guidance. This walkthrough provides one (of the many) possible solution to the challenges, without revealing any flags or passwords directly.
Learning Objectives
- Understand components and functions of a red team engagement.
- Learn how to properly plan an engagement based of needs and resources available and TTPs.
- Understand how to write engagement documentation in accordance to client objectives.
01 | Introduction
Question 1: Read the above and continue to the next task.
No answer needed
02 | Defining Scope and Objectives
The success of a red team engagement hinges on clearly defined client objectives and scope. These elements establish mutual expectations between the client and red team, providing structure and direction for the engagement.
-
Client Objectives:
- Clearly stated objectives are crucial for guiding the engagement.
- Discussing these objectives with the client ensures alignment of goals and expected outcomes.
- They form the foundation for all subsequent documentation and planning, ensuring a focused campaign from the outset.
-
Engagement Types:
- Engagements can be categorized into two main types: internal/network penetration tests (general approach) or focused adversary emulation (FAE) tests targeting specific APT groups (e.g., APT38 in finance sectors).
-
Scope of Engagement:
- The scope is set by the client and may outline what cannot be done (e.g., data exfiltration restrictions) or what can be targeted.
- Specific details vary but are crucial for planning and execution.
-
Analysis and Planning:
- From a red team perspective, understanding deeper implications of objectives and scope is essential.
- Dynamic problem-solving approaches are necessary, starting from a bare reading of the client's guidelines.
In essence, defining clear objectives and scope ensures effective engagement execution, while considering different assessment types and analyzing implications helps in delivering tailored solutions.
Question 1: Read the example client objectives and answer the questions below.
No answer needed
Question 2: What CIDR range is permitted to be attacked?
10.0.4.0/22
Question 3: Is the use of white cards permitted? (Y/N)
Y
Question 4: Are you permitted to access "*.bethechange.xyz?" (Y/N)
N
03 | Rules of Engagement
Rules of Engagement (RoE) are a legally binding document that outlines client objectives and scope, establishing clear expectations between the client and red team. This document serves as the first official agreement in the engagement process, requiring authorization from both parties. It can also be supported by Non-Disclosure Agreements (NDAs).
The format and content of RoE are crucial, as it is a legally binding contract. Each RoE structure varies based on specific client needs and typically includes standard sections such as Executive Summary, Purpose, References, Scope, Definitions, Rules of Engagement and Support Agreement, Provisions, Requirements, Restrictions, and Authority, Ground Rules, Resolution of Issues/Points of Contact, Authorization, Approval, and Appendix.
While the RoE is a summary, further planning is necessary to expand upon its details and client objectives.
Question 1: Once downloaded, read the sample document and answer the questions below.
No answer needed
Question 2: How many explicit restriction are specified?
3
Question 3: What is the first access type mentioned in the document?
Phishing
Question 4: Is the red team permitted to attack 192.168.1.0/24? (Y/N)
N
04 | Campaign Planning
"The RedTeam Guide Engagement checklist acts as a more generalized approach to planning a campaign and information needed."
Campaign planning for red team engagements involves using information from client objectives and Rules of Engagement (RoE) to create detailed plans. Each plan type is adapted from military operational documents and serves different purposes in outlining what the red team will do:
-
Engagement Plan | An overarching description of technical requirements
- Concept of Operations (CONOPS)
- Resource and personnel requirements
- Timelines
-
Operations Plan | Expands on the Engagement Plan with specific details
- Operators involved
- Known information
- Responsibilities
-
Mission Plan | Provides exact commands and execution times
- Commands to run
- Time objectives
- Responsible operator
-
Remediation Plan | Outlines post-campaign procedures
- Reporting processes
- Remediation consultation
Question 1: Read the above and move on to engagement documentation.
No answer needed
05 | Engagement Documentation
Engagement documentation extends campaign planning by officially recording ideas and thoughts. While some plans don't require formal documentation and can be as simple as an email, others are more detailed.
Technical overview of the campaign plans
-
Engagement Plan
- CONOPS (Concept of Operations) | A non-technical overview explaining how the red team meets client objectives and targets them.
- Resource Plan| Includes timelines and requirements for personnel, hardware, and cloud resources needed for success.
-
Operations Plan
- Personnel Information | Details employee requirements.
- Stopping Conditions | Explains when and why the red team should halt operations during an engagement.
- RoE (Rules of Engagement) | Optional, depending on specific needs.
- Technical Requirements | Outlines necessary knowledge for the red team's success.
-
Mission Plan
- Command Playbooks | Exact commands and tools to run, including when, why, and how they should be executed. This is especially useful in larger teams with diverse skill levels.
- Execution Times | Specific times for beginning different stages of an engagement, which can include exact timings for tool execution.
- Responsibilities/Roles | Assigns tasks and roles to team members.
-
Remediation Plan (optional)
- Report | Summarizes engagement details and presents findings.
- Remediation/Consultation | Outlines how clients will address identified issues, which can be included in the report or discussed in meetings.
The key points are about structuring documentation to support campaign execution and post-engagement actions, balancing formality based on plan complexity.
Question 1: Read the above and move on to the upcoming engagement specific tasks.
No answer needed
06 | Concept of Operations
The Concept of Operations (CONOPS) serves as a high-level overview within an engagement plan, akin to an executive summary. It is designed to provide a clear and concise understanding of the engagement proceedings for both business or client reference purposes and to guide further campaign planning by the red team.
Key elements of a CONOPS
- Client Name | Identifies the specific client or organization involved.
- Service Provider | Refers to the entity conducting the engagement.
- Timeframe | Specifies the duration during which the engagement takes place.
- General Objectives/Phases | Outlines the main objectives and stages of the engagement.
- Other Training Objectives (Exfiltration) | Details secondary goals, such as exfiltration processes.
- High-Level Tools/Techniques Planned | Lists key tools or methodologies to be used during the engagement.
- Threat Group to Emulate | Identifies the specific threat group being emulated.
The CONOPS should be written at a semi-technical level, ensuring it is accessible to readers with minimal technical expertise while still providing sufficient detail for the red team to extend their planning processes. The document must be clear and concise, avoiding overly complex information that could hinder understanding for non-technical stakeholders.
Holo Enterprises has hired TryHackMe as an external contractor to conduct a month-long network infrastructure assessment and security posture. The campaign will utilize an assumed breach model starting in Tier 3 infrastructure. Operators will progressively conduct reconnaissance and attempt to meet objectives to be determined. If defined goals are not met, the red cell will move and escalate privileges within the network laterally. Operators are also expected to execute and maintain persistence to sustain for a period of three weeks. A trusted agent is expected to intervene if the red cell is identified or burned by the blue cell throughout the entirety of the engagement. The last engagement day is reserved for clean-up and remediation and consultation with the blue and white cell.
The customer has requested the following training objectives: assess the blue team's ability to identify and defend against live intrusions and attacks, Identify the risk of an adversary within the internal network. The red cell will accomplish objectives by employing the use of Cobalt Strike as the primary red cell tool. The red cell is permitted to use other standard tooling only identifiable to the targeted threat.
Based on customer security posture and maturity, the TTP of the threat group: FIN6, will be employed throughout the engagement.
Question 1: Read the example CONOPS and answer the questions below.
No answer needed
Question 2: Based on customer security posture and maturity, the TTP of the threat group: FIN6, will be employed throughout the engagement.
No answer needed
Question 3: How long will the engagement last?
1 Month
Question 4: How long is the red cell expected to maintain persistence?
3 Weeks
Question 5: What is the primary tool used within the engagement?
Cobalt Strike
07 | Resource Plan
The Resource Plan is a document within the engagement plan that follows the Concept of Operations (CONOPS). It provides specific details related to dates, knowledge requirements, and resource needs, extending the high-level overview provided by the CONOPS.
Key elements of the Resource Plan
- Header | General heading for the document.
- Engagement Dates
- Reconnaissance Dates
- Initial Compromise Dates
- Post-Exploitation and Persistence Dates
- Miscellaneous Dates
- Knowledge Required (Optional)
- Reconnaissance
- Initial Compromise
- Post-Exploitation
- Resource Requirements
- Personnel
- Hardware
- Cloud Resources
- Miscellaneous Resources
The Resource Plan should be clear, concise, and to the point, avoiding unnecessary details while ensuring all required information is efficiently communicated.
Here is an example Resource Plan provided by THM.
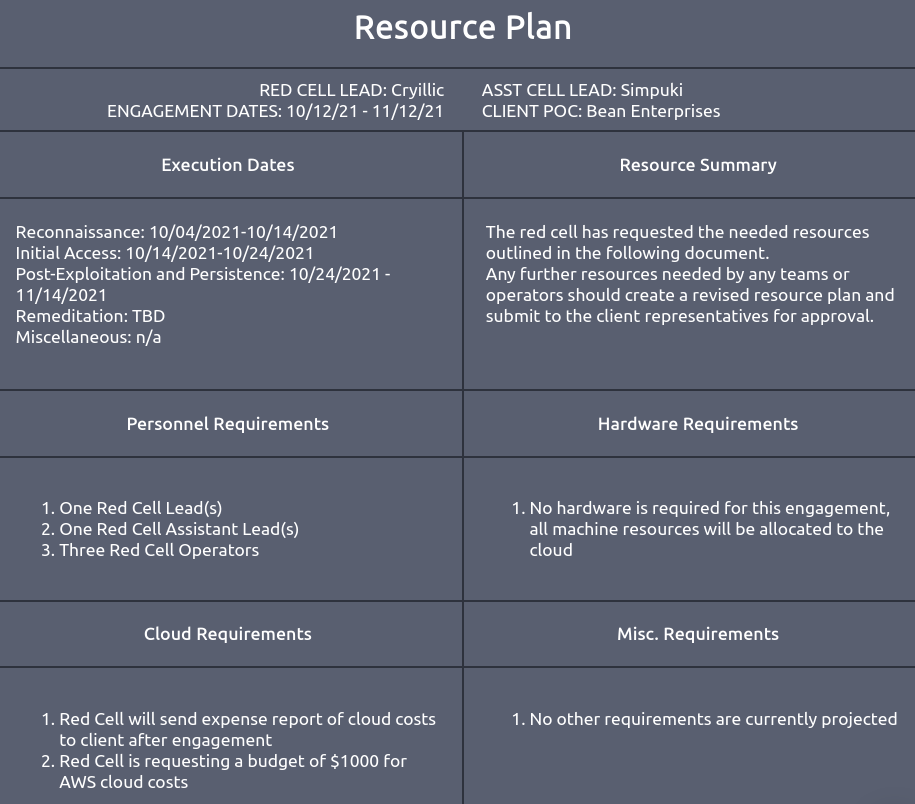
Question 1: Navigate to the "View Site" button and read the provided resource plan. Once complete, answer the questions below.
No answer needed
Question 2: When will the engagement end? (MM/DD/YYYY)
11/14/2021
Question 3: What is the budget the red team has for AWS cloud cost?
$1000
Question 4: Are there any miscellaneous requirements for the engagement? (Y/N)
N
08 | Operations Plan
The Operations Plan is a detailed document within the engagement plan that expands upon the Concept of Operations (CONOPS) and Resource Plan by providing specific details about the actions and activities during the engagement. It may optionally include the Rules of Engagement (ROE) and stopping conditions.
Key elements of the Operations Plan
- Halting/Stopping Conditions | Procedures for ceasing operations if necessary.
- Required/Assigned Personnel | Overview of personnel involved in the engagement.
- Specific TTPs and Attacks | Detailed list of tactics, techniques, and procedures planned.
- Communications Plan | Summary of communication methods, like vectr.io, Email or Slack
- Rules of Engagement (Optional) | Guidelines for conduct during the engagement.
The Operations Plan should be clear, detailed, and structured to ensure all necessary information is efficiently communicated without unnecessary verbosity.
Here is an example Operations Plan provided by THM.
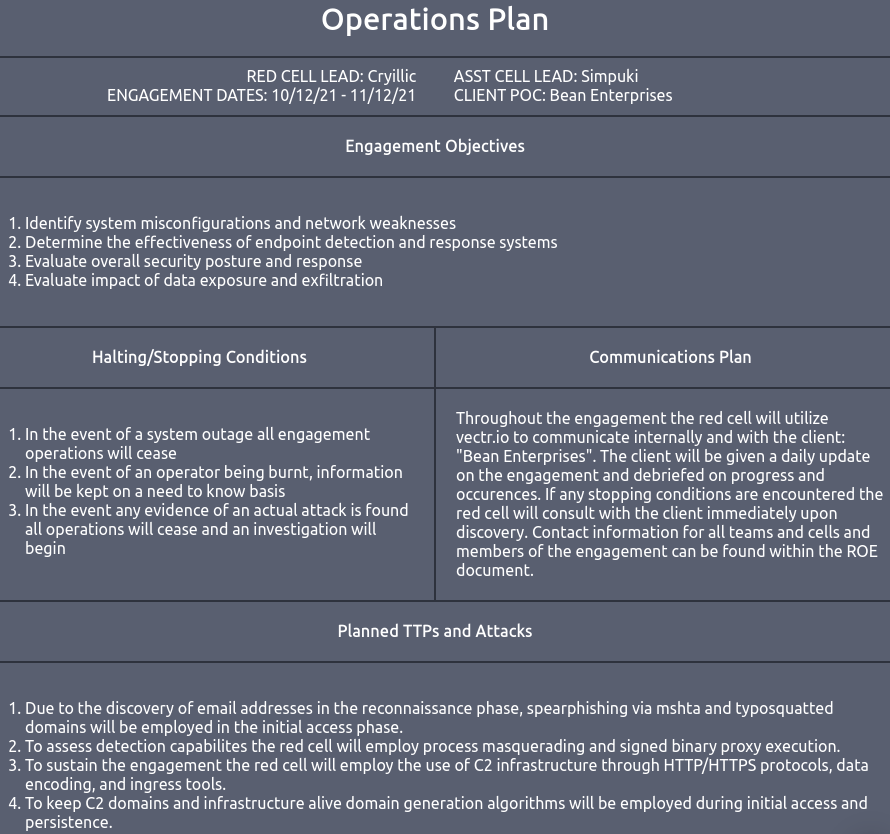
Question 1: Navigate to the "View Site" button and read the provided operations plan. Once complete, answer the questions below.
No answer needed
Question 2: What phishing method will be employed during the initial access phase?
Spearphishing
Question 3: What site will be utilized for communication between the client and red cell?
vectr.io
Question 4: If there is a system outage, the red cell will continue with the engagement. (T/F)
F
09 | Mission Plan
The Mission Plan is a detailed, cell-specific document within the engagement plan that outlines the exact actions operators must complete. It draws on information from previous plans and assigns specific tasks to operators.
Key elements of the Mission Plan
- Objectives | The primary goals of the mission.
- Operators | Overview of personnel involved in executing the mission.
- Exploits/Attacks | Specific tactics, techniques, and procedures planned.
- Targets | Details about users, machines, or objectives being targeted.
- Execution Plan Variations | Alternative methods for conducting the mission.
The Mission Plan is intended for internal use and can vary in structure and detail depending on the team's preferences. It focuses on clarity and specificity without unnecessary complexity, ensuring that operators have a clear understanding of their roles and actions during the engagement.
Here is an example Mission Plan provided by THM.

Question 1: Navigate to the "View Site" button and read the provided mission plan. Once complete, answer the questions below.
No answer needed
Question 2: When will the phishing campaign end? (mm/dd/yyyy)
10/23/2021
Question 3: Are you permitted to attack 10.10.6.78? (Y/N)
N
Question 4: When a stopping condition is encountered, you should continue working and determine the solution yourself without a team lead. (T/F)
F
10 | Conclusion
Internal documents and unique team methodologies are essential for red teams' operations. The framework guides without being a manual; clear planning and documentation are crucial for meeting client objectives.
Question 1: Read the above and continue learning!
No answer needed