0103 | Red Team Threat Intel

Red Teaming | Red Team Threat Intel | Summary:
In this room, you'll learn how to harness the power of threat intelligence in red team engagements. You'll discover how to apply threat intel concepts to drive your campaigns, understand key frameworks like TIBER-EU, and practice using threat intelligence to inform your tactics, techniques, and procedures (TTPs).
Through interactive challenges and real-world examples, you'll gain a deeper understanding of how to create a threat-intel-driven campaign that sets you apart as a red team operator.
This summary is NOT intended to replace the original content, but rather serve as supplementary material. It provides a quick summary or personal notes for individuals who may be struggling with the original content.
Learning Objectives
- Understand the basics of threat intelligence and how it can be applied to red team engagements.
- Learn how to create a threat-intel-driven campaign.
- Use frameworks to understand concepts and leverage threat intelligence.
1 | Introduction
Threat Intelligence (TI) and Cyber Threat Intelligence (CTI) refer to information gathered about an adversary's tactics, techniques, and procedures (TTPs). This intelligence is primarily used by defenders to enhance their ability to detect and respond to threats. From an offensive standpoint, such intelligence can be utilized by "red cells" (teams simulating attacks) to assist in creating realistic adversarial simulations, aiding in the preparation and understanding of potential attacker behaviors.
2 | What is Threat Intelligence
Cyber Threat Intelligence (CTI) entails gathering information on Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs) from adversaries. These IOCs and TTPs are often sourced from Information Sharing Analysis Centers (ISACs), which can also be considered as platforms for threat intelligence. CTI provides chronological data that helps defenders analyze potential threats.
Traditionally, blue teams use CTI to detect adversarial behavior by leveraging IOCs. Conversely, red teams utilize this intelligence to evaluate how effectively defenders can counter potential attacks, particularly focusing on Advanced Persistent Threats (APTs) and their documented TTPs. This approach ensures a comprehensive understanding of both the threat landscape and defensive capabilities.
3 | Applying Threat Intel to the Red Team
The red team utilizes Cyber Threat Intelligence (CTI) to gather and analyze adversaries' behaviors, employing tools such as MITRE ATT&CK, TIBER-EU, and OST Map. These platforms categorize Tactics, Techniques, and Procedures (TTPs) based on factors like threat groups, kill chain phases, and objectives.
This intelligence is instrumental in planning attacks, allowing the red team to develop tooling and mimic adversary behavior. The focus lies in understanding and replicating specific stages of an attack cycle, guided by categorized TTPs.
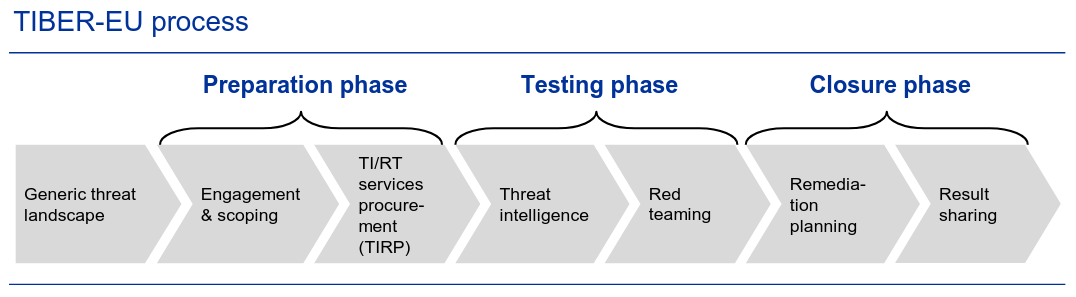
4 | The TIBER-EU Framework
The TIBER-EU (Threat Intelligence-based Ethical Red Teaming) framework developed by the European Central Bank emphasizes the integration of threat intelligence into ethical red team practices. Its unique aspect is the "Testing" phase, which involves using threat intelligence to enhance the red team's ability to simulate attacks and evaluate an organization's resilience against cyber threats.
This framework serves as a best practice guide rather than providing actionable steps.
The following picture depicts the TIBER-EU Process taken straight out from their white paper.
5 | TTP Mapping
The process of TTP mapping involves associating an adversary's Tactics, Techniques, and Procedures (TTPs) with a standard cyber kill chain to facilitate effective red teaming. The goal is to emulate adversaries accurately during engagements.
- Adversary Selection
- Factors such as target industry, attack vectors, country of origin, and other criteria are considered
- Kill Chain Framework
- TTPs from frameworks like MITRE ATT&CK are mapped to specific phases of the kill chain, aiding in planning and execution.
- Tools and Resources
- MITRE ATT&CK | Provides TTPs categorization, with tools like ATT&CK Navigator aiding in visualization.
- OST Map | Offers a visual link between threat actors and their TTPs.
- Other Platforms | Resources such as Mandiant Advantage, Ontic, and CrowdStrike Falcon supplement TTP mapping efforts.
This structured approach ensures red teams can emulate adversaries effectively, enhancing the accuracy and realism of cyber engagement exercises.
6 | Other Red Team Applications of CTI
Continuous Threat Intelligence (CTI) is not only used to gather insights about adversaries but also plays a crucial role during red teaming engagements. CTI can be applied to emulate adversaries' behaviors in multiple ways.
-
C2 Traffic Manipulation
- Red teams can modify Command & Control (C2) traffic to mimic that of the targeted adversary. This involves creating "malleable profiles" based on intelligence gathered from sources like Indicators of Compromise (IOCs), packet captures, or Intelligence Sharing and Analysis Centers (ISACs). These profiles allow operators to manipulate aspects of C2 traffic, such as headers, URIs, server responses, and more, making the traffic indistinguishable from that of the actual adversary.
-
Analysis of Adversary Behavior
- CTI can also be used to analyze how adversaries behave when using specific malware or tools. For example, a red team can study an adversary's custom dropper by analyzing its network traffic, system calls, and objectives. This intelligence can then be used to develop offensive tooling that exhibits similar behaviors or incorporates vital indicators of the adversary's tools.
By leveraging CTI during engagements, red teams can create more realistic and contextually accurate simulations, enhancing their ability to emulate adversaries effectively.
7 | Creating a Threat Intel Driven Campaign
The process of creating a well-planned, threat-intel-driven red team campaign involves the following steps:
-
Identify Framework and General Kill Chain | Start by choosing a relevant framework or kill chain model (e.g., MITRE ATT&CK) to structure your campaign.
-
Determine Targeted Adversary | Identify an adversary based on specific criteria, such as industry, sector, or known behaviors.
-
Identify Adversary’s TTPs and IOCs | Gather the adversary's Tactics, Techniques, and Procedures (TTPs) as well as their Indicators of Compromise (IOCs). This can be done through open-source intelligence, threat reports, or other sources.
-
Map Threat Intelligence to a Kill Chain | Use the gathered TTPs and IOCs to map out how the adversary would operate within the chosen framework or kill chain.
-
Draft and Maintain Engagement Documentation | Prepare detailed documentation that outlines the campaign's objectives, tactics, techniques, and resources needed for execution.
-
Determine and Use Needed Engagement Resources | Identify and procure necessary tools, platforms, domains, and other assets required to execute the campaign effectively.
By following a structured approach, red teams can create a comprehensive and realistic simulation tailored to the targeted adversary’s behavior, enhancing their ability to conduct effective exercises or defensive measurements.
8 | Conclusion
When planning a red team engagement, it's essential to focus on adversary emulation and leverage threat intelligence to identify adversaries and their behaviors. Each red team will have its methodology for collecting and analyzing threat intelligence in real-world scenarios.
It’s crucial to approach the engagement from multiple perspectives—offensive, defensive, and adversarial—to ensure comprehensive planning. Threat intelligence allows the red team to delve deeper into an adversary's behavior by using blue team methodologies to their advantage. This enables more accurate emulation of adversaries' tactics, techniques, and procedures, ultimately enhancing the effectiveness of the engagement.