THM | Phishing

Red Teaming | Phishing | Summary:
This room focuses on teaching the basics of phishing attacks and their importance in red team engagements.
The room takes you through various aspects of phishing, including setting up infrastructure, writing convincing emails, and using different tools like GoPhish and techniques like Typosquatting to trick targets into opening malicious links or attachments.
Please note that this write-up is NOT intended to replace the original room or its content, but rather serve as supplementary material for those who are stuck and need additional guidance. This walkthrough provides one (of the many) possible solution to the challenges, without revealing any flags or passwords directly.
01 | Brief
Question 1: I'm ready to learn!
No answer needed
02 | Intro To Phishing Attacks
Social engineering is a psychological manipulation technique where individuals are tricked into revealing information or performing actions by exploiting human weaknesses such as curiosity or greed. Phishing, a form of social engineering, often uses email to deceive people into divulging personal information or executing malicious code.
Phishing emails typically appear from trusted sources and may include tempting offers or links leading to bogus websites. Spear-phishing targets specific individuals or organizations, making it harder to detect with standard security tools like spam filters. This method is commonly used by red teams for vulnerability assessments.
Other phishing methods include smishing (via SMS) and vishing (through phone calls). An example scenario illustrates how an attacker can exploit a local business opportunity to trick employees into revealing credentials via email, highlighting the effectiveness of these techniques in exploiting human vulnerabilities.
The below example scenario shows how an employee of a company could be tricked into revealing their credentials.
- The attacker locates the physical location of the target business.
- The attacker then looks for nearby food suppliers and discovers a company called Ultimate Cookies!
- The Attacker registers the domain name ultimate-cookies.thm
- The attacker then crafts an email to their target, tempting them with an offer of receiving some free cookies if they sign up to the website. Because the victim has heard of this local company, they are more likely to trust it.
- The victim then follows the link in the email to the fake website created by the attacker and registers online. To keep things simple, the victim reuses the same password for all their online accounts.
- The attacker now has the victim's email address and password and can log onto the victim's company email account. The attacker could now have access to private company information and also have somewhere to launch another phishing attack against other employees.
Question 1: What type of psychological manipulation is phishing part of?
social engineering
Question 2: What type of phishing campaign do red teams get involved in?
spear-phishing
03 | Writing Convincing Phishing Emails
Phishing emails rely on three key components to deceive victims: the sender's email address, subject lines, and content.
- Sender's Email Address:
- Spoofed from well-known brands or contacts by using domains that appear legitimate.
- Gathered through OSINT tactics, such as analyzing social media, Google searches, business websites, and LinkedIn profiles of the target to identify potential spoofing targets.
- Subject Line:
- Designed to be urgent, attention-grabbing, or curious, prompting immediate action.
- Examples include warnings about compromised accounts, packages, payroll information, or published photos.
- Content:
- Mimics legitimate brands or contacts by researching their email templates, logos, and signatures.
- Uses anchor text to disguise malicious links as trustworthy references to the spoofed brand or contact.
- example |
<a href="http://spoofsite.thm">Click Here</a>or<a href="http://spoofsite.thm">https://onlinebank.thm</a>
The aim is to create convincing emails that minimize suspicion, increasing the likelihood of victims revealing sensitive information or executing malicious actions.
Question 1: What tactic can be used to find brands or people a victim interacts with?
OSINT
Question 2: What should be changed on an HTML anchor tag to disguise a link?
anchor text
04 | Phishing Infrastructure
To effectively launch a phishing campaign, several key components and tools are essential:
-
Domain Name | Register an authentic-looking domain or mimic another's, to ensure legitimacy.
-
SSL/TLS Certificates | Implement these to add authenticity to the domain, enhancing the site's trustworthiness.
-
Email Server/Account | Utilize either an email server setup or an SMTP provider to send phishing emails from believable addresses.
-
DNS Records (SPF, DKIM, DMARC) | Configure these records to improve email deliverability and prevent spam flags, mimicking legitimate domains' practices.
-
Web Server/Hosting | Set up web servers or purchase hosting for phishing sites, with SSL/TLS adding an extra layer of authenticity.
-
Analytics Tools | Implement tracking tools to monitor campaign success, including emails sent, opened, clicked, and data from phishing sites regarding personal information or malicious downloads.
-
Automation and Tools | Use frameworks like GoPhish for simplified campaign setup and additional tools such as SET (Social Engineering Toolkit) for creating spear-phishing attacks and fake websites to deceive victims into revealing credentials.
- GoPhish | (Open-Source Phishing Framework) | SMTP server, email templates, email scheduling, analytics
- SET | (Social Engineering Toolkit) | spear-phishing, fake versions of common websites
This infrastructure and toolset are crucial for executing a well-organized and effective phishing campaign.
Question 1: What part of a red team infrastructure can make a website look more authentic?
SSL/TLS Certificates
Question 2: What protocol has TXT records that can improve email deliverability?
DNS
Question 3: What tool can automate a phishing campaign and include analytics?
GoPhish
05 | Using GoPhish
Sending Profiles Demo Setup
- Name | Local Server
- Interface Type | SMTP
- From | [email protected]
- Host | 127.0.0.1:25
- Username and Password are left blank
- Check "Ignore Certificate Errors"
- Everything else left blank > Click on "Save Profile"
Landing Pages Demo Setup
- Name | ACME Login
- HTML Source
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>ACME IT SUPPORT - Admin Panel</title>
<style>
body { font-family: "Ubuntu", monospace; text-align: center }
div.login-form { margin:auto; width:300px; border:1px solid #ececec; padding:10px;text-align: left;font-size:13px;}
div.login-form div input { margin-bottom:7px;}
div.login-form input { width:280px;}
div.login-form div:last-child { text-align: center; }
div.login-form div:last-child input { width:100px;}
</style>
</head>
<body>
<h2>ACME IT SUPPORT</h2>
<h3>Admin Panel</h3>
<form method="post">
<div class="login-form">
<div>Username:</div>
<div><input name="username"></div>
<div>Password:</div>
<div><input type="password" name="password"></div>
<div><input type="submit" value="Login"></div>
</div>
</form>
</body>
</html> - Click "Source" button again > Check both "Capture Submitted Data" and "Capture Passwords"
- Everything else is left blank > "Save Page"
Email Templates Demo Setup
- Name | Email 1
- Subject | New Message Received
- Click "link" button
- Display Text |
https://admin.acmeitsupport.thm - Protocol |
<other> - URL |
{{.URL}}| placeholder for the actual link
- Display Text |
- Content/Text
Hello,
You've received a new message, please log in to the admin portal to view it <link>.
Many Thanks
Online Team- Check "Add Tracking image"
- Leaver everything else blank > "Save Template"
Users & Groups Demo Setup
- Name | Targets
- "Add" for every email enty
- Leave everything else blank > "Save changes"
Campaigns Demo Setup
- Name | Campaign One
- EmailTemplate | Email 1
- Landing Page | ACME Login
- URL |
http://<MACHINE_IP> - Launch Date | Set it to 2 days ago (adjust it to your needs)
- Sending Profile | Local Server
- Groups | Targets
- press "Launch Campaign" > "Launch" on "Are You Sure" prompt
Question 1: What is the password for Brian?
<password>
06 | Droppers
Droppers are malicious tools used in phishing attacks that trick victims into downloading and running software on their systems. These droppers may be presented as useful or legitimate applications, such as codecs for video playback or software to open specific files. Despite being non-malicious themselves, they can pass antivirus checks, making them stealthy delivery mechanisms for harmful payloads.
Once installed, droppers facilitate the download of malicious software from a server, which is then installed on the victim's computer. This payload can establish a connection back to the attacker's infrastructure, enabling unauthorized access and control over the system. From here, attackers may exploit the local network, leading to significant security breaches for both individuals and organizations.
In summary, droppers are stealthy tools used to deliver malicious software, bypassing standard security measures.
Question 1: Do droppers tend to be malicious?
nay
07 | Choosing A Phishing Domain
Choosing the perfect phishing domain is essential for achieving psychological impact on targets. Key strategies:
- Expired Domains | Purchasing a domain with history can improve its score in spam filters, as new domains often face more scrutiny.
- Typosquatting | This involves registering domain names that closely resemble target domains through methods
- Misspelling |
goggle.com - Additional Period |
go.ogle.com - Switching numbers for letters |
g00gle.com - Phrasing |
googles.com - Additional Word |
googleresults.com
- Misspelling |
- TLD Alternatives | Using different top-level domains (e.g., ".co.uk" instead of ".com") can make the phishing site appear more legitimate.
- IDN Homograph Attacks/Script Spoofing | Leveraging Unicode character similarities across languages allows attackers to register domains that resemble others, exploiting visual similarities to deceive victims.
- example | Unicode character
U+0430(Cyrillic small letter a) similar to Unicode characterU+0061(Latin small letter a)
- example | Unicode character
These strategies help create domain names that are convincing and increase the likelihood of a successful phishing attack.
Question 1: What is better, using an expired or new domain? (old/new)
old
Question 2: What is the term used to describe registering a similar domain name with a spelling error?
typosquatting
08 | Using MS Office In Phishing
During phishing campaigns, attackers frequently use Microsoft Office documents (Word, Excel, PowerPoint) as vectors. These files may contain macros, which can be legitimate but also exploited by attackers. When victims enable macros upon opening such attachments, malicious actions can occur, including malware installation or establishing unauthorized network connections, leading to potential system compromise.
An example illustrates this tactic
- an email from a spoofed "Human Resources" address directs the recipient to open an Excel file, which may contain macros that exploit the victim's computer. This method leverages psychological tactics to trick individuals into enabling potentially dangerous content, highlighting the importance of caution with Office attachments in phishing scenarios.
Question 1: What can Microsoft Office documents contain, which, when executed can run computer commands?
macros
09 | Using Browser Exploits
Browser exploits are a method used by attackers to gain control over victims' computers. These exploits target vulnerabilities in web browsers, such as Internet Explorer/Edge, Firefox, Chrome, or Safari, which can be exploited by visiting malicious websites. While less common, these attacks can be effective, particularly when targeting outdated software that cannot be updated due to compatibility issues, as is often the case in large institutions like education, government, or healthcare.
An example of such an exploit is CVE-2021-40444 from September 2021, which allowed code execution simply by visiting a website. Attackers may trick victims into visiting these sites through deceptive emails or messages, enabling them to perform malicious actions on the compromised computer.
Browser exploits can be a potent tool for attackers when exploiting vulnerabilities in outdated software, highlighting the importance of keeping browsers and systems updated to mitigate such risks.
Question 1: Which recent CVE caused remote code execution?
CVE-2021-40444
10 | Phishing Practical
Question 1: What is the flag from the challenge?
<flag>
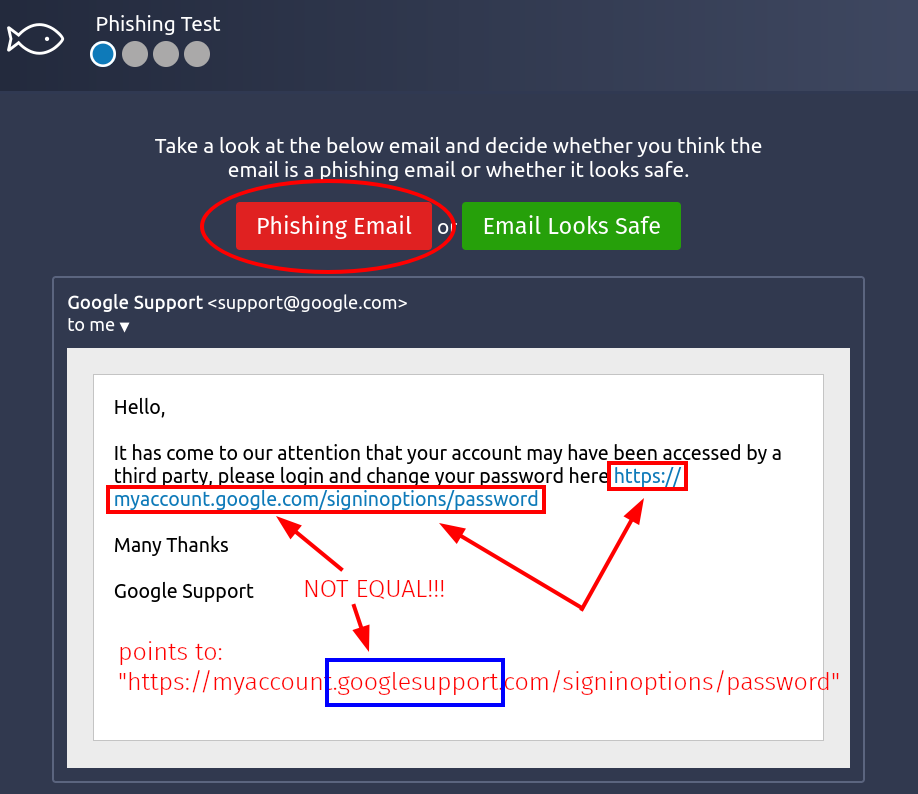
- Phishing Test | Scenario 1
- The domain names for the displayed link and the actual/real link do NOT match
- Verdict | "Phishing Email"
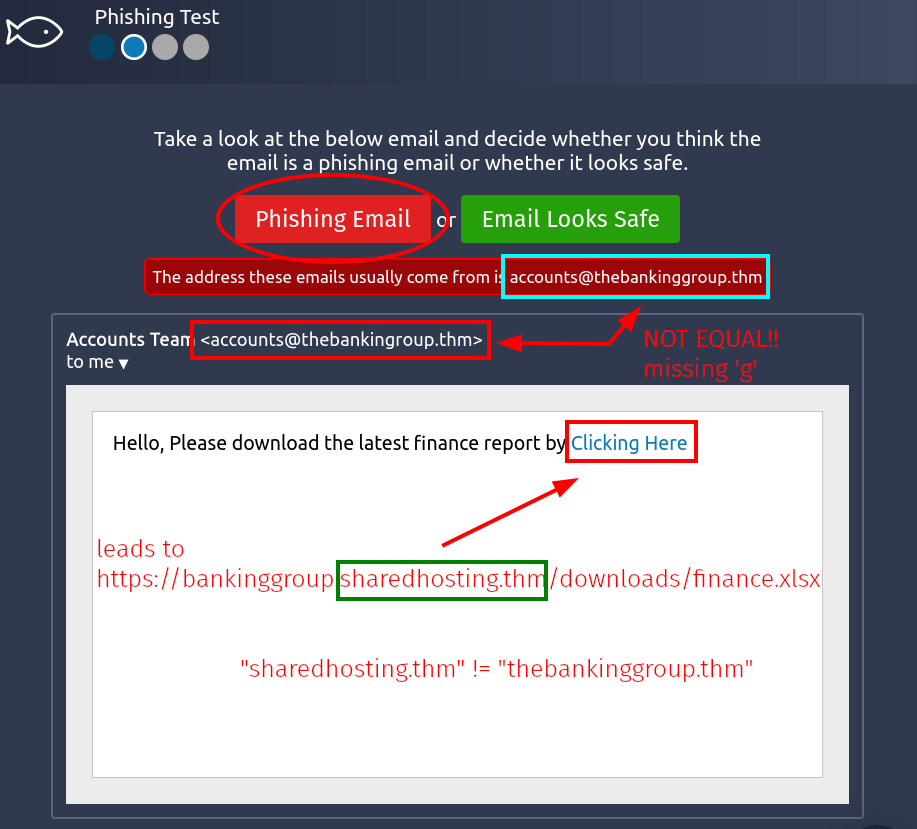
- Phishing Test | Scenario 2
- Issue-1 | There is a misspelling (one less 'g') in the sender's address.
- Issue-2 | The actual link leads to the
sharedhosting.thmdomain instead ofthebankinggroup.thmdomain. - Verdict | "Phishing Email"
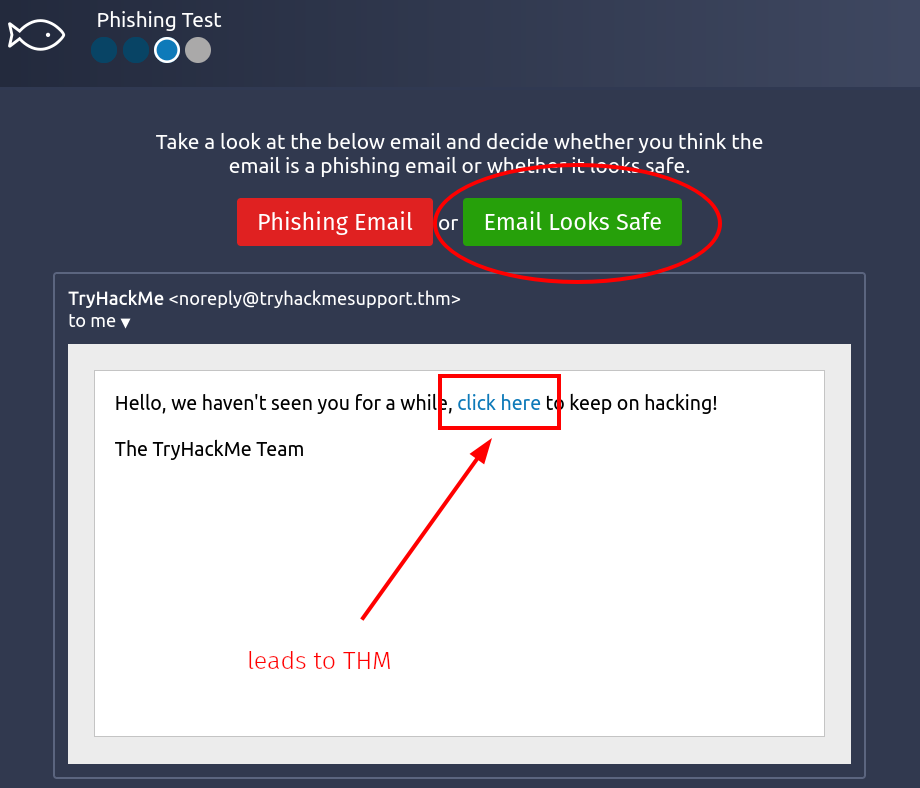
- Phishing Test | Scenario 3
- The actual link leads to the real THM site and both the sender and the content look normal.
- Verdict | "Email Looks Safe"
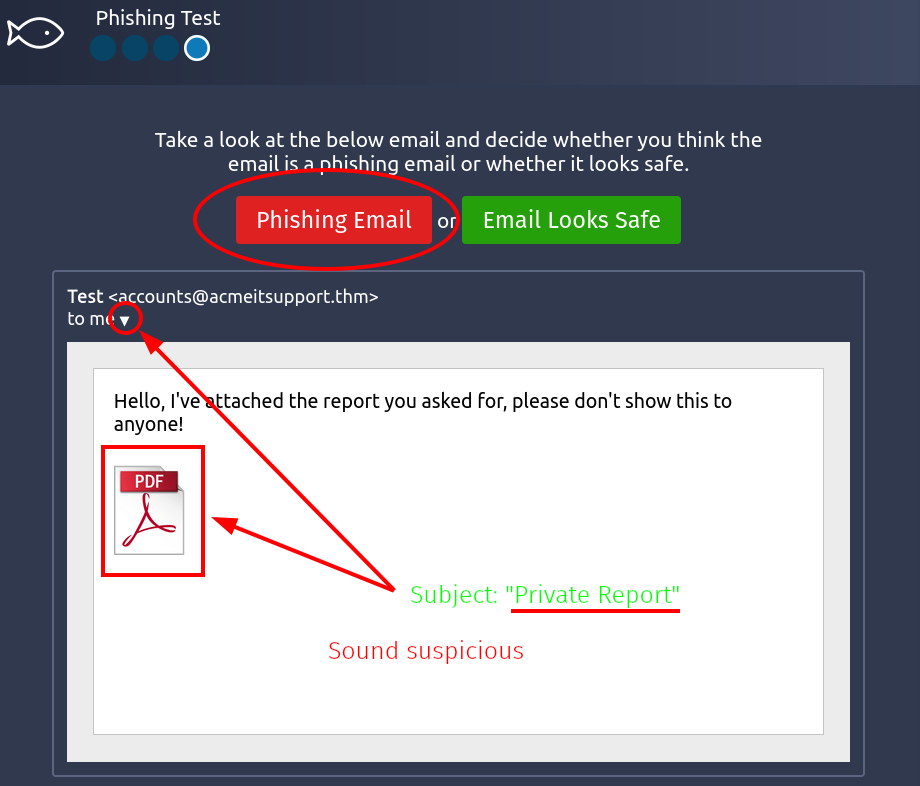
- Phishing Test | Scenario 4
- Issue-1 | Suspicious Subject ("Private Report")
- Issue-2 | Attached PDF file
- Verdict | "Phishing Email"
Do NOT forget to grab the flag!